Social Networks: Cybersecurity Best Practices
Igor Draytsel, Chief Information Security Officer
Share with a Friend
All fields required where indicated (*)In this second blog of our Cybersecurity series, we discuss the security risks faced when engaging on Social Networks and offer suggestions for mitigating against such risks.
*the URLs included in this blog are safe to visit
Is Your Data at Risk?
On September 13, 2022, former Twitter Chief Information Security Officer (CISO) Peiter Zatko, also known by his hacker name “Mudge”, testified in Senate. From Zatko’s testimony, we learned that the FBI recently informed Twitter of an employee who was an intelligence agent planted by China’s Ministry of State Security. This is not the first time that Twitter had been infiltrated by agents of foreign governments. In prior years, Twitter had found government agents from India, China and Saudi Arabia among its workforce. Zatko told senators that Twitter doesn’t understand how much data it collects about its users, why it collects that data and how that data is supposed to be used. The company stores users’ IP addresses, emails, personally identifiable information (PII), locations and device details. “Anybody with access inside Twitter… could go rooting through and find this information and use it for their own purposes.” Zatko further stated that Twitter is unable to control the data it collects about its customers, that is, your data.
Facebook has been similarly plagued by losing users’ data for years. In April 2021, 533 million users’ PII was compromised and published online. Recently, 1.5 billion Facebook users' personal information was offered for sale on a popular hacking-related forum. The details of this alleged leak are being investigated.
In 2021, 500 million LinkedIn users’ data was offered for sale by hackers, with 2 million records immediately made public to prove the leak.
And while the data leaks list goes on, social networks present other dangers.
Don’t Just Click “Accept”
In 2010, white-hat hackers Robin Casey and Thomas Ryan conducted an experiment. They registered a LinkedIn profile for a fictional character they named Robin Sage. The profile stated that Sage was a cyber-threat analyst at Naval Network Warfare Command in Norfolk, Virginia, a job that requires top government clearance. Sage was allegedly 25 years old and an MIT graduate with ten years of work experience.
25 years old / 10 years of cyber-threat analyst experience – notice any red flags?
Despite the apparent inconsistencies, Sage’s profile collected hundreds of connections, including security contacts from military and intelligence communities. Sage was offered government and corporate jobs (including at Google and Lockheed Martin) and speaking arrangements at cybersecurity conferences. Through Sage’s connections, Casey and Ryan could learn about the locations of military units and the relationships between government organizations. The experiment revealed that a fake online personality could easily fool even seasoned security professionals. To learn more about “Robin Sage” experiment visit Robin Sage Experiment - Wikipedia.
In recent developments, tens of fake CISO profiles have been registered on LinkedIn targeting Fortune 500 companies.
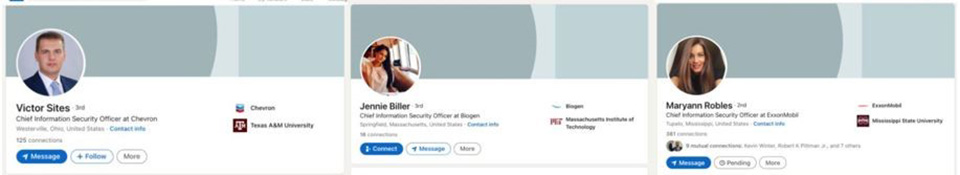
Victor Sites’ profile claims to be CISO for Chevron and Maryann Robles is registered as CISO for ExxonMobil, while the true CISOs for the two companies are different individuals.
At this point, it is unclear who the actors behind these fake profiles are or how exactly the actors plan to use them.
To learn more about fake CISO profiles visit Fake CISO Profiles on LinkedIn.
So, What Do We Learn From the Above?
- Regularly check if your personal email or phone number were part of any known data breach or leak. Visiting Have I Been Pwned can be a good start.
- Change passwords for your LinkedIn and other leaked email accounts.
- Use password manager to create strong passwords and store them securely.
- Enable multi-factor authentication everywhere it is feasible.
- Learn to share less online. Don’t post anything you wouldn’t want made public knowledge.
- Always tighten the privacy settings for your online accounts.
- When asked to connect on social, do not just click “Accept”. Beware of suspicious messages and connection requests from strangers. If you don’t know the person, do some basic research first. Be careful who you choose as your next contact.
Disclosures:
Please note that VanEck may offer investments products that invest in the asset class(es) or industries included in this commentary.
This is not an offer to buy or sell, or a recommendation to buy or sell any of the securities/financial instruments mentioned herein. The information presented does not involve the rendering of personalized investment, financial, legal, or tax advice. Certain statements contained herein may constitute projections, forecasts and other forward looking statements, which do not reflect actual results, are valid as of the date of this communication and subject to change without notice. Information provided by third party sources are believed to be reliable and have not been independently verified for accuracy or completeness and cannot be guaranteed. VanEck does not guarantee the accuracy of third party data. The information herein represents the opinion of the author(s), but not necessarily those of VanEck.
All investing is subject to risk, including the possible loss of the money you invest. As with any investment strategy, there is no guarantee that investment objectives will be met and investors may lose money. Diversification does not ensure a profit or protect against a loss in a declining market. Past performance is no guarantee of future results.
© Van Eck Securities Corporation, Distributor, a wholly owned subsidiary of Van Eck Associates Corporation.